3.5. Setting up clients
Client management is carried out on the CLIENT MANAGEMENT page. To switch to the client manager, click on the “clients” button at the upper left corner of the panel:
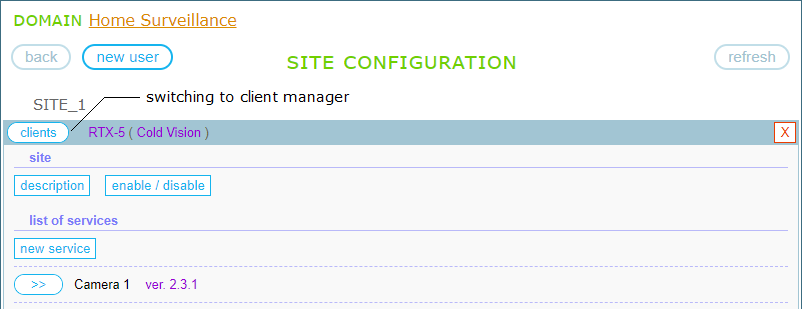
Here, you can set up clients for users authorized on the site:
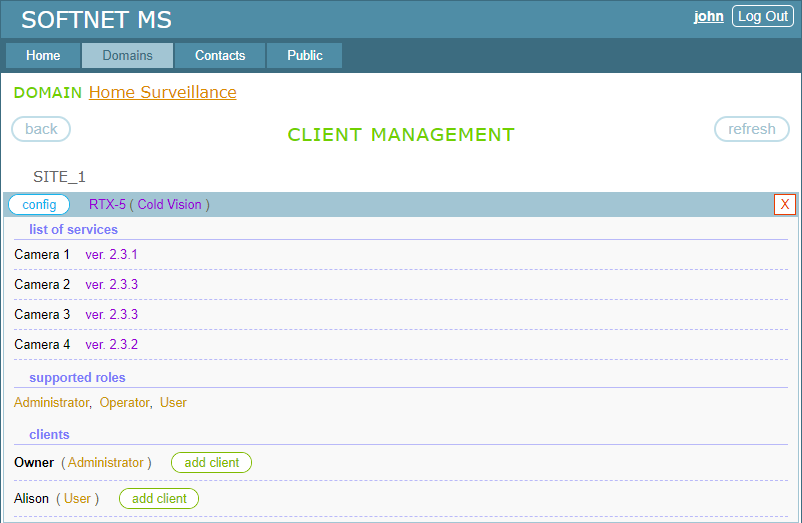
First, we create a client entity for the Owner user to set up a remote control application. Clicking the “add client” button, which is to the right of Owner, creates a client entity:
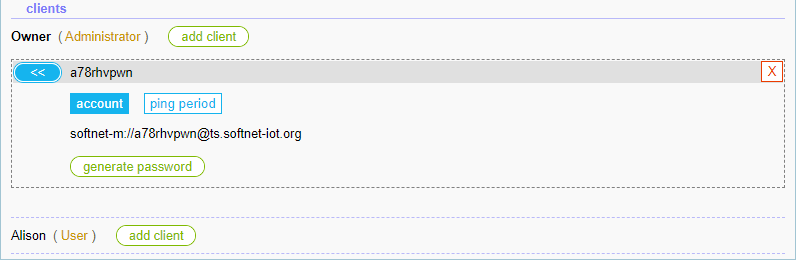
Clicking the “generate password” button generates a client password:
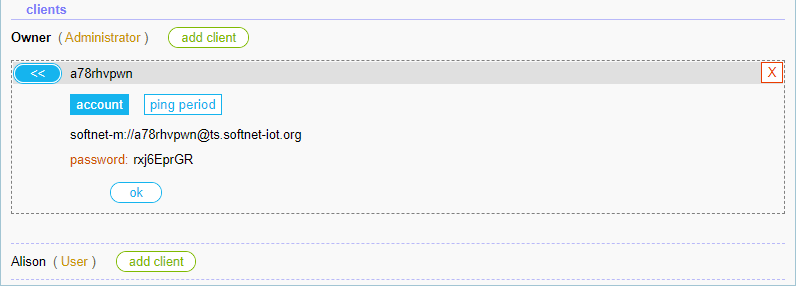
Now, we have the client URI and password:
softnet-m://a78rhvpwn@ts.softnet-iot.org
password: rxj6EprGR
We provide them to the client application and connect it to the site. If everything is Ok, the client gets online and the client entity takes the following view:
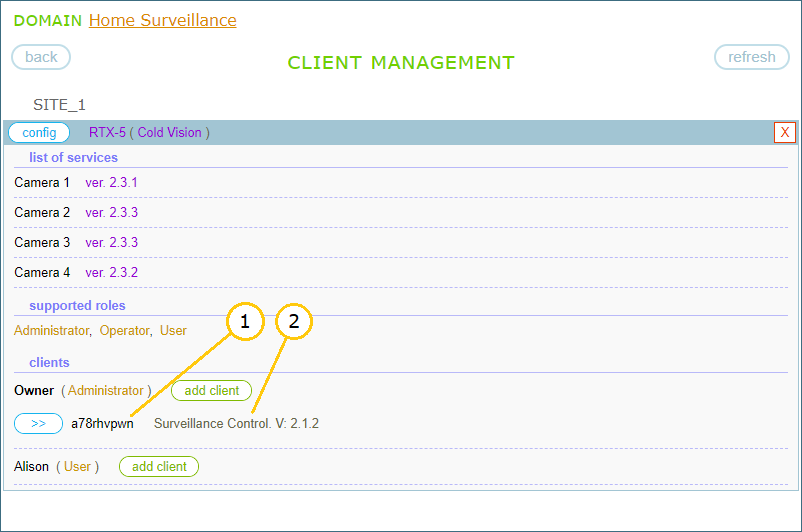
Typically, a client is represented on the site by a client key and client description. The client key is created by the site, but the client description is provided by the client itself. The latter is optional but highly desirable parameter. It usually contains the functional description of the client and its version, which helps the owner in administrative tasks. In case of our example, the client is represented by:
- client key: a78rhvpwn
- description: Surveillance Control. V: 2.1.2
We’ve assigned the Adminstrator role to Owner, so the remote control application we’ve set up can interact with the IP cameras with administrative rights.
Now we’ll create a client entity for Alison and set up a remote control application on this entity. Clicking the “add client” button, which is to the right of Alison, creates a client entity:
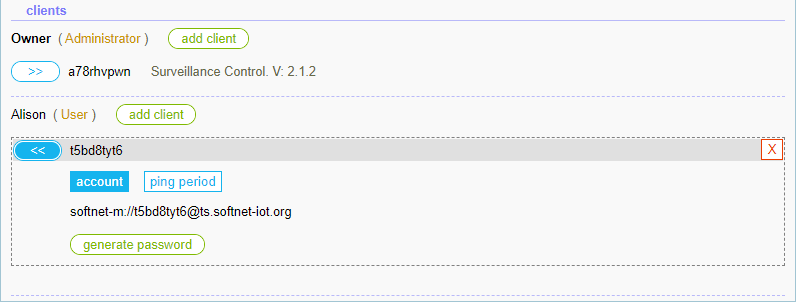
Then clicking on the “generate password” button creates a password:
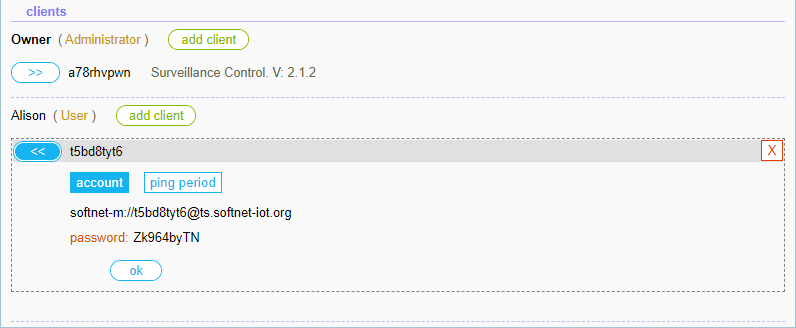
We have the client URI and password:
softnet-m://t5bd8tyt6@ts.softnet-iot.org
password: Zk964byTN
We provide them to the Alison’s client application and connect it to the site. If everything is Ok, the client gets online and the client entity takes the following view:
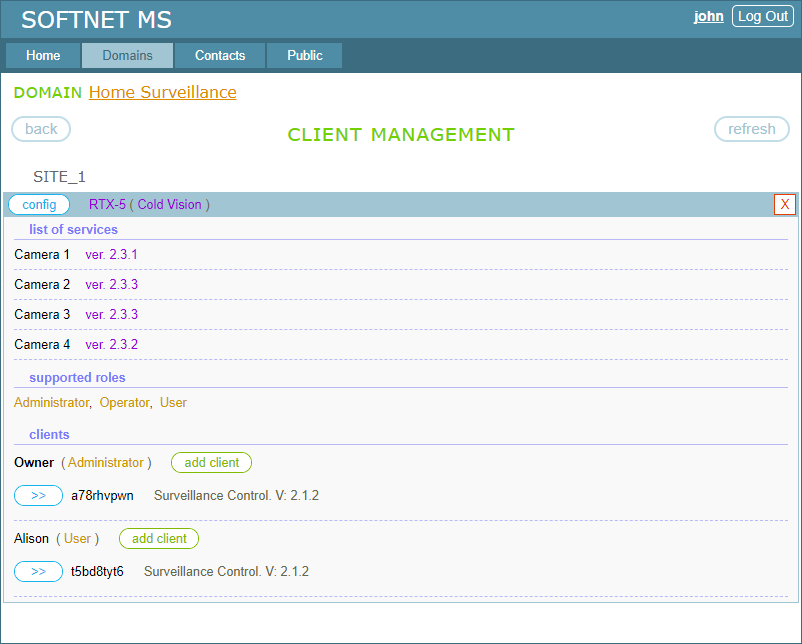
We have two remote control applications set up on the site. Each will interact with the IP cameras in accordance with the role we assigned to the appropriate user in the previous section.
It’s worth noting that the mechanism of Contacts offers a much more efficient way to share access to devices with other persons/organizations. This is a topic of chapter 8.